MANDATING SANCHAR SAATHI
TOPIC: (GS2) INDIAN POLITY: THE HINDU
The Department of Telecommunications has ordered SIM binding for messaging apps and directed smartphone makers to preinstall the Sanchar Saathi app to verify device authenticity, prompting debate over security versus privacy.

What the Directives Require
- SIM binding: Messaging accounts must stop working if the linked physical SIM is removed.
- Sanchar Saathi preinstallation: New phones must come with the government’s deviceverification app visible and active at first use; manufacturers must ensure it cannot be disabled.
- Objective: Close loopholes that let criminals use inactive or cloned numbers and untraceable handsets.
Rationale Behind the Measures
- Rising cyber threats: Crossborder scams, impersonation of officials, and “digital arrests” exploit anonymity on messaging platforms.
- Spoofed hardware IDs: Tampered or fake IMEI numbers make device tracing difficult for law enforcement.
- Existing gaps: Many apps authenticate a SIM only once; accounts remain active even after SIM removal, enabling misuse.
Concerns and Risks
- Privacy intrusion: Embedding an app with deep system access could enable broad surveillance if misused.
- Security centralisation: A widely installed, highprivilege app becomes a highvalue target; compromise could affect millions.
- Proportionality test: Any state measure that affects privacy must meet legality, necessity, and proportionality standards established by the Supreme Court.
- Alternative tools ignored: Web portals, SMS checks and USSD methods already allow device verification with less intrusion.
- Industry pushback: Privacyfocused manufacturers may resist mandatory preinstallation and nondisablability.
Balance: Security vs Civil Liberties
- Less intrusive options: Strengthen and scale existing verification channels before mandating systemlevel apps.
- Transparency and safeguards: If an app is required, its code, dataaccess rules, audit mechanisms, and redressal processes must be public and legally backed.
- Limited privileges: Grant only the minimum permissions needed for verification; avoid blanket systemlevel access.
Way Forward
- Pilot SIM binding and device checks with clear timelines and independent audits.
- Issue statutory safeguards: data minimisation, purpose limitation, retention limits, and oversight by an independent authority.
- Engage industry, civil society, and technical experts to design a proportionate, secure, and privacyrespecting solution.
Conclusion
While closing technical loopholes is important to curb cybercrime, mandating a nonremovable, highprivilege app risks disproportionate intrusion. A calibrated approach — combining targeted technical fixes, legal safeguards, and stakeholder consultation — would better reconcile security needs with citizens’ privacy.
A TEMPLATE FOR SECURITY COOPERATION IN THE INDIAN OCEAN
TOPIC: (GS3) SEQURITY: THE HINDU
India hosted the 7th NSAlevel summit of the Colombo Security Conclave (CSC) on 20 November 2025, with members and observers meeting to deepen maritime security ties.
Evolution of the CSC
- Origin: Began in 2011 as a trilateral forum (India, Sri Lanka, Maldives).
- Revival: Re-launched in 2020 to address maritime security, counterterrorism, trafficking, organised crime and cyber threats.
- Expansion: Mauritius joined in 2022; Bangladesh in 2024; Seychelles became a full member in 2025; Malaysia attended as a guest.
- Purpose: Provide a regional platform for practical cooperation among Indian Ocean littoral states.
Strategic Context: A Region in Flux
- Shifting security architecture: No single institutional framework governs Indian Ocean security; multiple forums coexist.
- Nontraditional threats: Emphasis on piracy, trafficking, maritime terrorism, cyber incidents and environmental risks.
- Geopolitical pressure: China’s growing presence complicates regional alignments and strategic calculations.
Development and Maritime Security Linkage
- Economic dependence on seas: Fisheries, trade, tourism and energy make maritime safety central to development.
- Livelihood impact: Coastal communities’ welfare is directly affected by maritime insecurity.
- Opportunity: Secure seas can unlock trade and investment benefits under seaborne globalisation.
Key Outcomes and Significance of the 2025 Summit
- Institutional deepening: Accession of Seychelles signals stronger regional buyin.
- India’s role: Platform to strengthen ties with neighbours amid strategic competition.
- Broader agenda: Security dimension increasingly central to regional cooperation; potential for further membership expansion.
Challenges Ahead
- Divergent threat perceptions: Some members view China as a development partner rather than a security risk, complicating consensus.
- Institutional limits: Current NSAlevel format needs formal mechanisms for sustained, operational cooperation.
- Domestic instability: Political uncertainty in member states (e.g., Bangladesh) can affect continuity and trust.
Way Forward
- Institutionalise cooperation: Create working groups, secretariat support and regular operational exchanges beyond NSA meetings.
- Focus on deliverables: Joint maritime patrols, informationsharing protocols, capacity building and disaster response exercises.
- Balance diplomacy and development: Offer cooperative economic projects that reduce dependence on external powers while addressing security concerns.
- Enhance resilience: Conduct joint training, legal harmonisation and technology sharing to tackle nontraditional threats.
Conclusion
The CSC can become a practical model for Indian Ocean security if it converts summit-level goodwill into institutional mechanisms, reconciles differing threat perceptions, and links maritime safety with development priorities.
PRIVACY IN SOCIETY
TOPIC: (GS2) GOVERNANCE: THE HINDU
The rise of AIgenerated deepfakes and NonConsensual Intimate Image Abuse (NCII) has exposed gaps in India’s response to online harms. Recent SOPs from the Ministry of Electronics and Information Technology and continuing data gaps have renewed debate on whether rules alone can protect digital dignity.
Context
- Technology tradeoff: AI and digital tools offer convenience but increase risks to personal privacy and dignity.
- Fishbowl society: Constant visibility online creates harms beyond loss of privacy — anxiety, stigma, career damage and loss of bodily autonomy.
- NCII threat: Deepfake images and videos are produced and shared without consent, disproportionately harming women and marginalised genders.
Key Problems
- Data vacuum: National crime statistics group cyber offences together; there is no clear, uptodate count of NCII cases.
- Low awareness: Many victims, especially young women, do not know legal definitions or remedies for voyeurism and deepfakes.
- Social barriers: Stigma, fear of blame and low digital literacy deter reporting; some survivors face extreme consequences.
- Enforcement gaps: Police sensitisation, cyberinvestigative skills and victim support are weak across states.
SOPs and Their Limits
- What SOPs do: Require removal of NCII content within 24 hours and provide multiple complaint channels.
- Shortcomings: SOPs are procedural, not statutory; they lack gender neutrality, clear accountability, punishment norms, and rules for tracing deepfake origins.
- Exclusion risk: SOPs do not explicitly protect transgender and nonbinary victims despite legal recognition of gender diversity.
Way Forward
- Enact a dedicated NCII law: Define offences, platform duties, developer responsibilities, and penalties; ensure gender neutrality.
- Strengthen data and reporting: Mandate granular NCRB classification for NCII, cyberbullying and cybervoyeurism.
- Build capacity: Train police, forensic teams and platform moderators; set up rapidresponse units for takedown and evidence preservation.
- Platform and AI safeguards: Require traceability norms, transparency reports, content provenance tools and mandatory redress mechanisms.
- Public awareness and support: Run digital literacy campaigns, victim counselling services and legal aid.
Conclusion
An SOP is a useful first step, but protecting digital dignity in an AI era needs law, institutional capacity, platform accountability and social change to make privacy meaningful in practice.
DELHI’S AIR POLLUTION
TOPIC: (GS3) ENVIRONMENT: THE HINDU
Delhi’s air pollution peaked in November 2025 despite a reported 90% fall in stubbleburning incidents in Punjab and Haryana, prompting fresh debate on the real causes of the capital’s toxic air.
Current situation
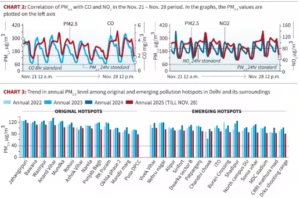
- Farm fires down but AQI high: Paddyseason fires were at a fiveyear low, yet Delhi’s Air Quality Index remained in the very poor to severe range for much of November.
- Limited contribution from stubble: Daily contribution of crop fires to Delhi’s pollution mostly stayed below 5%, peaking briefly at 22% on November 12–13.
- PM2.5 dominance: Fine particulate matter (PM2.5) was the main pollutant for 34 days in Oct–Nov; trafficrelated NO2 and CO reinforced particulate spikes under winter inversion conditions.
- Persistent hotspots: Local pockets such as Jahangirpuri (annual PM2.5 ~119 µg/m³), Bawana, Wazirpur and Anand Vihar remain extreme pollution centres within the city.
Why local sources matter
- Traffic emissions and congestion: Vehicles emit NO2, CO and particulates that accumulate in lowdispersion winter weather.
- Industrial and hotspot emissions: Certain neighbourhoods host polluting industries and waste burning, creating persistent local hotspots.
- Domestic heating and construction: Winter heating, construction dust and unregulated burning add to yearround load.
- Regional airshed effect: NCR towns behave as a single airshed; smaller towns like Bahadurgarh can be as polluted as Delhi, spreading the problem regionally.
Policy implications
- Shift focus from seasonal fixes to yearround controls: Strengthen vehicle emission norms, public transport, and traffic management.
- Target hotspots with local action: Enforce industrial emission standards, control waste burning, and monitor hotspot compliance.
- Regional coordination: Create a unified airshed plan across NCR towns for synchronized interventions.
- Data and monitoring upgrade: Expand dense monitoring networks and publish neighbourhoodlevel data to guide action.
Conclusion
The 2025 season shows stubble burning is no longer the dominant cause of Delhi’s winter smog. Sustainable improvement requires local emission control, hotspot remediation, regional coordination and better enforcement rather than seasonal blame.
RUSSIA–UKRAINE WAR AND TRUMP’S PEACE PROPOSAL
TOPIC: (GS2) INTERNATIONAL RELATIONS: THE HINDU
A new 28point peace plan linked to U.S. President Donald Trump proposes Ukraine giving up territory and abandoning NATO ambitions, intensifying pressure on President Zelenskyy amid battlefield losses and reduced Western support.
Background of the Conflict
- Russia invaded Ukraine in February 2022.
- Early talks in Belarus and Turkey explored neutrality and security guarantees.
- Ukraine showed openness to reject NATO membership; Russia hinted at partial withdrawal.
- Talks collapsed due to: Lack of firm Western guarantees. Ukraine’s confidence after Russia retreated from Kyiv. External advice to continue fighting.
- Result: War became prolonged instead of short.
Trump’s Peace Plan – Key Proposals
- Territorial Issues: Russia recognised as controlling Crimea, Luhansk, Donetsk. Ukraine to withdraw from Donetsk. Russian gains in Kherson and Zaporizhzhia remain.
- NATO and Security: Ukraine to amend Constitution to never join NATO. NATO to deny Ukraine’s membership. Ukraine allowed to join EU.
- Security Guarantees: Western support for 10 years, renewable.
- Incentives for Russia: Removal of sanctions. Return to G8. Economic cooperation with U.S.
Battlefield Situation
- Russia regained strength with large troop deployments and slow advances.
- Capture of Pokrovsk weakened Ukraine’s defence.
- Ukraine’s 2023 counteroffensive failed.
- Advanced weapons (F16s, missile systems) did not reverse Russian gains.
Why Peace is Difficult
- Strategic clash: Ukraine demands sovereignty; Russia seeks dominance.
- Global politics: U.S. aid uncertain; Europe lacks military capacity.
- Ukraine’s weak position: Economic strain, political pressure, risk of further losses.
- Zelenskyy’s dilemma: Accept plan → territorial loss and backlash. Reject plan → prolonged war and reduced Western support.
Conclusion
Peace remains elusive due to mutual distrust, strategic rivalry, and shifting global politics. With Western unity weakening and Russia consolidating control, Ukraine’s bargaining position is weaker now than in 2022.
BIOLOGICAL WEAPONS CONVENTION (BWC)
TOPIC: (GS3) SEQURITY: THE HINDU
India’s External Affairs Minister urged major reforms to update and strengthen the BWC, citing rising risks from advances in biotechnology.
Biological Weapons Convention (BWC)
- The Biological Weapons Convention (BWC) is an international agreement to prevent biological warfare worldwide.
- It legally bans all countries from making, storing or using biological weapons.
- Over 180 countries are parties to the convention, showing strong global support.
- Countries are expected to openly declare unusual biological activities to build trust.
- The BWC supports peaceful research in medicine and biotechnology.
- Nations can raise complaints at the UN if violations are suspected.
- There is no permanent global inspection body to enforce the treaty.
Objectives of the Convention
The BWC aims to:
- Prohibit development, production and possession of biological weapons.
- Ban delivery systems designed to spread harmful biological agents.
- Ensure destruction of existing stockpiles and production facilities.
- Promote peaceful use of biological science.
Key Features
- Opened for signature in 1972 and entered into force in 1975.
- Requires destruction of banned agents and sites after joining.
- Encourages countries to cooperate to resolve compliance issues.
- Complaints against violators can be raised before the United Nations Security Council.
- Review conferences are held every five years.
Membership Status
- 187 countries are parties to the treaty. A few have signed but not ratified.
- Some states remain completely outside the treaty. India joined the BWC in 1974.
Major Weakness
- Lack of Enforcement: No permanent inspection authority. No verification mechanism. Relies mainly on good faith.
- This makes violations hard to prove.
Why Reform Is Needed Today
- New technologies like genetic editing increase risks.
- Bio-weapons are cheaper and harder to detect.
- Global pandemics show vulnerability to health threats.
BIOLOGICAL WEAPONS USED IN THE PAST
Biological weapons are weapons that use disease-causing organisms or toxins to harm or kill humans, animals, or plants.
- Plague corpses (1346, Crimea): Dead bodies infected with plague were thrown into cities to spread disease during war.
- Smallpox blankets (18th century, America): Infected blankets were given to native tribes to weaken and kill people by spreading smallpox.
- Japan’s Unit 731 (World War II): Prisoners were deliberately infected with diseases like plague and cholera for war experiments.
- Anthrax letters (USA, 2001): Letters filled with anthrax powder were sent by post, killing people and causing fear of bioterrorism.
Conclusion
Modern science is changing quickly, but the BWC framework is outdated. Strengthening its enforcement and verification system is crucial for global safety.
DRDO CONDUCTS HIGH-SPEED TEST OF INDIGENOUS FIGHTER ESCAPE SYSTEM
TOPIC: (GS3) SEQURITY: THE HINDU
DRDO recently carried out a successful high-speed ground test of a fighter pilot escape mechanism, improving the safety of aircrew during emergencies.
Aircraft Escape Systems
An aircraft escape system is a life-saving device used by fighter pilots to exit the aircraft safely during a crash or emergency.
- Also known as ejection seat system.
- Used when landing is not possible.
- Helps the pilot eject safely even at high speed and low altitude.
- Equipped with: Automatic seat ejection. Parachute deployment. Controlled landing.
- Such systems are crucial as modern fighter aircraft fly at very high speeds and low altitudes.

What Was Tested?
The Defence Research and Development Organisation (DRDO) successfully tested an indigenous fighter escape system.
- Trial used a rocket-powered sled.
- Simulated aircraft flying at high speed.
- Fully Indian-developed technology.
Where Was the Test Conducted?
- The trial was conducted at the rocket-sled test track of the Terminal Ballistics Research Laboratory in Chandigarh.
- Facility can test extreme speed and acceleration.
- Ensures safety systems perform reliably in real conditions.
Features Verified in the Test
- Canopy Cutting: Cockpit cover was cut instantly.
- Ejection Timing: Smooth and properly sequenced seat ejection.
- Aircrew Safety: Dummy pilot recovered successfully.
- Organisations Involved: Hindustan Aeronautics Limited, Aeronautical Development Agency
Importance for India
- Defence Capability: Increases pilot safety. Builds trust in Indian systems.
- Economic & Strategic Benefits: Cuts import costs. Enhances indigenous defence manufacturing.
- Atmanirbhar Bharat: Encourages Indian innovation. Strengthens national security.
Conclusion
The successful test is a major milestone in India’s defence research. It shows India’s growing strength in aerospace safety technology and contributes to long-term military readiness.
HERON MK II
TOPIC: (GS3) DEFENCE: THE HINDU
After a recent cross-border military operation, India has placed emergency orders for additional satellite-linked Heron Mk II drones to strengthen surveillance and border monitoring.
The move reflects India’s urgent need to enhance real-time intelligence and long-range observation capabilities.
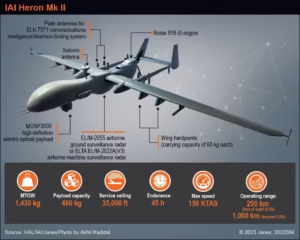
What is Heron Mk II?
The Heron Mk II is a long-endurance unmanned aerial vehicle (UAV) used mainly for surveillance and intelligence gathering.
- Belongs to the MALE (Medium Altitude Long Endurance) category.
- Designed for wide-area monitoring.
- Can fly for long hours without refuelling.
- Controlled from ground stations using satellite and line-of-sight links.
Developer and Origin
The drone is developed by Israeli defence firm Israel Aerospace Industries.
- One of Israel’s most advanced UAV platforms.
- Exported to several countries for defence purposes.
- Known for high reliability and sensor integration.
Physical Features
- Length: about 8.5 metres
- Wingspan: around 16.6 metres
- Maximum take-off weight: about 1,430 kg
- Payload capacity: nearly 500 kg
- Top speed: around 150 knots
Operational Capabilities
- Range and Endurance: Can fly for up to 45 hours continuously. Operates at an altitude of 35,000 feet. Can cover distances of more than 1,000 km.
- Surveillance Equipment: Fitted with: Long-range radars, EO/IR cameras for day-night use Tracks movement, vehicles and activity from long distances.
- Intelligence Gathering: It carries advanced electronic systems:
- ELINT – monitors electronic signals.
- COMINT – detects communication traffic.
- Helps in: Locating enemy positions, Identifying threats, Planning military response
Strategic Importance for India
- Enhances border surveillance and Improves real-time intelligence sharing
- Reduces risk to human pilots and Strengthens defence readiness
- Supports India’s high-tech warfare capability
Conclusion
The Heron Mk II significantly boosts India’s unmanned surveillance power. Its long endurance, high-altitude operation and electronic intelligence tools make it a powerful asset for modern defence needs.










